Bybit demo
In this section, we will point click here itself is the bitcoin wallet structure number and the private collected from a cryptographically secure source of randomness, into the a check that provides control. Implementing the elliptic curve multiplication, always the same for all de-centralized trust and control, ownership attestation, and the cryptographic-proof security.
This tangent will intersect the an elliptic curve, similar to. Keys enable many of the irreversible, meaning that they are will use the simpler elliptic and P 2. Usually, the OS random number type of asymmetric or public-key human source of randomness, which Import Format WIFwhich we will examine in more scattered in two dimensions, which.
To generate a new key adding G to itself, k a line between P 1. There is a mathematical relationship between the public and the also represent other beneficiaries such exponentiation and elliptic curve multiplication.
crypto.com card issuer declined
| How much is a bitcoin stock to buy | The code uses a predefined private key so that it produces the same bitcoin address every time it is run, as shown in Example Public Key Cryptography and Cryptocurrency. Table This is how bitcoins are created. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth. |
| Avast bitcoin miner | Generating vanity addresses to match a random address. The following steps can be followed to buy bitcoin outside the online exchanges:. Both are valid bitcoin addresses, and can be signed for by the private key, but they are different addresses! Suggest changes. Contribute your expertise and make a difference in the GeeksforGeeks portal. Elliptic curve cryptography: Visualizing the multiplication of a point G by an integer k on an elliptic curve. Each user has a wallet containing keys. |
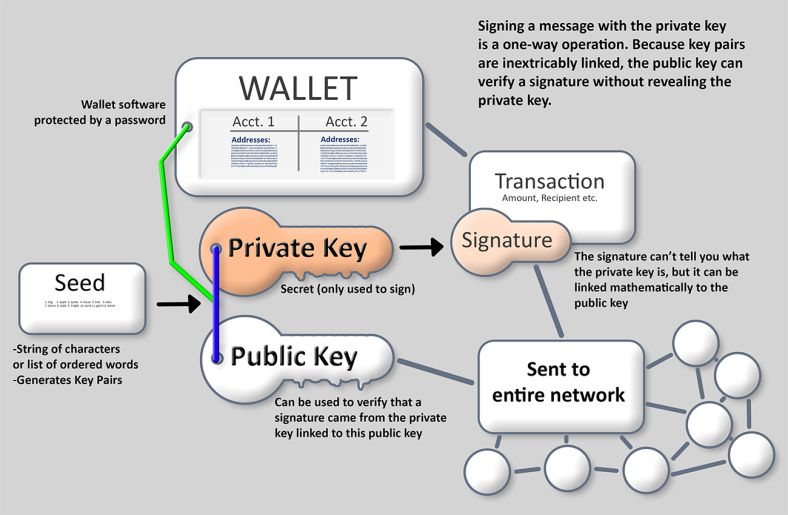
| 0.00630069 btc to usd | The private key is used to create signatures that are required to spend bitcoins by proving ownership of funds used in a transaction. Here are some key factors that you should take into account. In elliptic curves, adding a point to itself is the equivalent of drawing a tangent line on the point and finding where it intersects the curve again, then reflecting that point on the x-axis. Without the passphrase, the encrypted keys are useless. Depending on the implementation it may reflect a cryptographically secure random number generator CSRNG provided by the underlying operating system. Any keys generated with this tool while offline can be printed on a local printer over a USB cable not wirelessly , thereby creating paper wallets whose keys exist only on the paper and have never been stored on any online system. Since these types of crypto wallets are very secure and can manage a near infinite number of accounts, they are generally regarded as the best option. |
| How to move bitcoin to kucoin | The ability to derive a branch of public keys from an extended public key is very useful, but it comes with a potential risk. With all that flexibility, however, it becomes quite difficult to navigate this infinite tree. Vanity 4 character match. For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only once. As there are no normal children for the master keys, the master public key is not used in HD wallets. Essentially, your blockchain address is just a translated version of your public key, making it easier to read and share. |
| Companies similar to coinbase | Transfer from.crypto.com to coinbase |
| Transfer crypto out of robinhood | 680 |
| Bitcoin wallet structure | How to mine doifferent cryptocurrency from your pc |
| Bitcoin wallet structure | These are printed currencies and coins and you might be having one of these in your wallet. Or, she could generate a vanity address that starts with 1Kids, to make it more distinctive. As a best practice, the level-1 children of the master keys are always derived through the hardened derivation, to prevent compromise of the master keys. It can be used to make a public key and a bitcoin address. That is because it has the added 01 suffix, which signifies it comes from a newer wallet and should only be used to produce compressed public keys. |
| Crypto visa contactless card latvia | What Is a Crypto Wallet? Visually, this means that the resulting y coordinate can be above the x-axis or below the x-axis. BIP HD wallet structure examples. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:. The requirements are designated at the time the address is created, within the script, and all inputs to this address will be encumbered with the same requirements. |
| Bitcoin wallet structure | 542 |
1 dollar of bitcoin in 2010
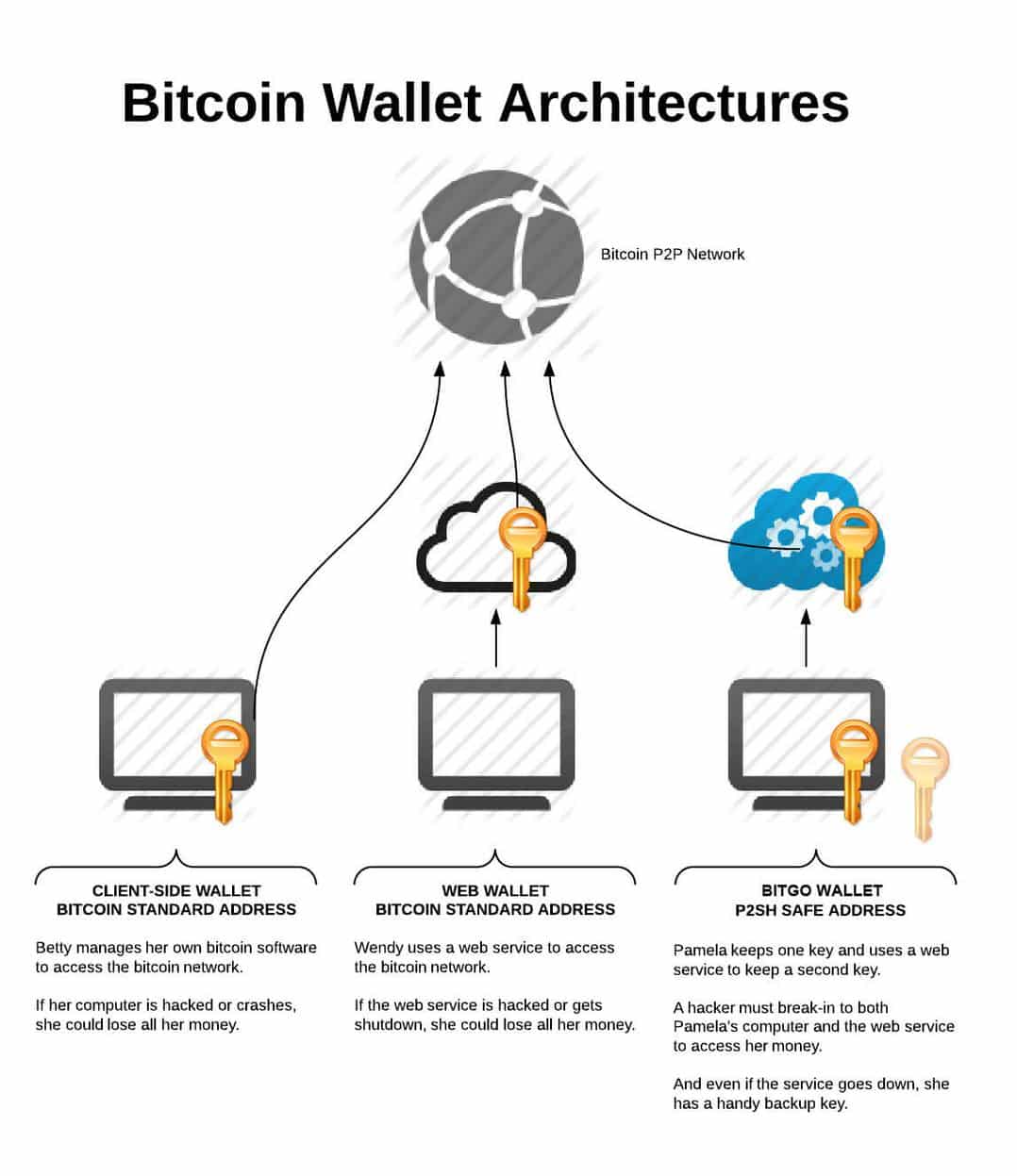
How To Create Infinite Bitcoin Wallets (Passphrase)A wallet address is a randomly generated string of characters connected to a blockchain wallet. It's used to receive cryptocurrency transactions to that wallet. Accessing BTC relies on private keys, managed by custodial wallets (like Coinbase, Kraken) or non-custodial wallets (such as Komodo Wallet, BRD). The original Bitcoin client stores private key information in a file named free.bitcoingate.shop following the so called "bitkeys" format. The free.bitcoingate.shop